Facebook 这个岗位虽然叫 Network Engineer,但是它的 OA 基本只考了 BGP 这一个协议,而且考得十分的深入。如果没有直接相关经历,可能很难通过它的考核。不过总结出的这份资料对我以后还是蛮有用的。
Computer Networks
Chapter 1
- Routing & forwarding:
- Routing: Determines source-destination route taken by packets;
- Forwarding: Move packets from router’s input to appropriate router output.
- Circuit switching (dedicated resources & not sharing) vs packet switching.
- Delay: dnodal = dproc + dqueue + dtrans + dprop
- dproc: Check bit errors, determine output;
- dqueue: Waiting at output link for transmission;
- dtrans: packet length / bandwidth;
- dprop: distance / speed of light.
- Layers:
- Application: Message;
- Transport: Segment;
- Network: Datagram;
- Link: Frame;
- Physical: Bits on the wire.
Chapter 2
- TCP & UDP:
- TCP: Reliable transport, flow control (won’t overwhelm receiver), congestion control (throttle sender when network overloaded), connection-oriented;
- UDP: Unreliable data transfer;
- SSL provides encrypted TCP connection (Integrity & authentication). SSL is at app layer.
- HTTP connections can be persistent (multiple objects over single TCP connection) or non-persistent (at most one object over single TCP connection, need at least 2 RTT).
- Client <– POP/IMAP/HTTP –> Mail server <– SMTP –> Mail server <– POP/IMAP/HTTP –> Client.
- DNS (Doomain name system) is an app-layer protocol. It’s distributed and hierarchical.
-
Iterated query (left) & recursive query (right):
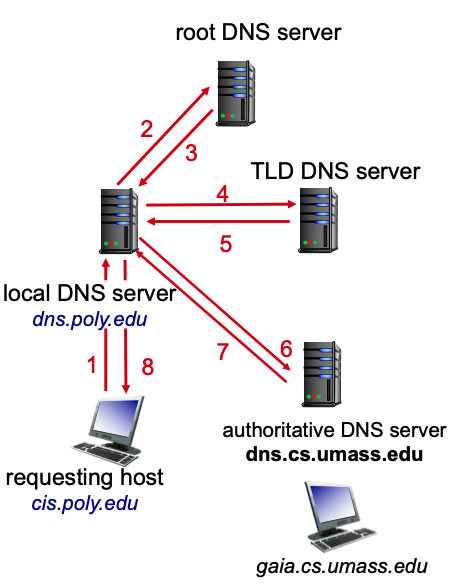
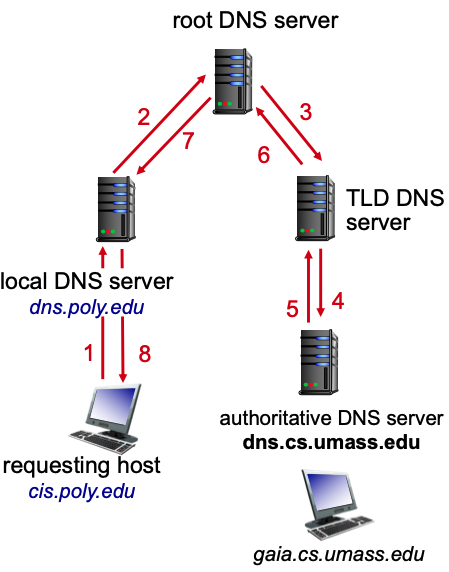
-
Types:
- A: Name: ranthot.cn, value: 8.8.8.8, type: A, TTL: …;
- NS: Name: ranthot.cn, value: ns1.registrar.com, …;
- CNAME: Name: ranthot.cn, value: servereast.backup2.ranthot.cn, …;
- MX: Name: ranthot.cn, value: mailserver.ranthot.cn, ….
-
Chapter 3
- Transport layer: Logical communication between processes; Network layer: Logical communication between hosts.
- Multiplexing & demultiplexing:
- Multiplexing: Handle data from multiple sockets, add transport header;
- Demultiplexing: Use header info to deliver received segments to correct socket.
- Internet checksum: Add together, add carryout, then one’s complement.
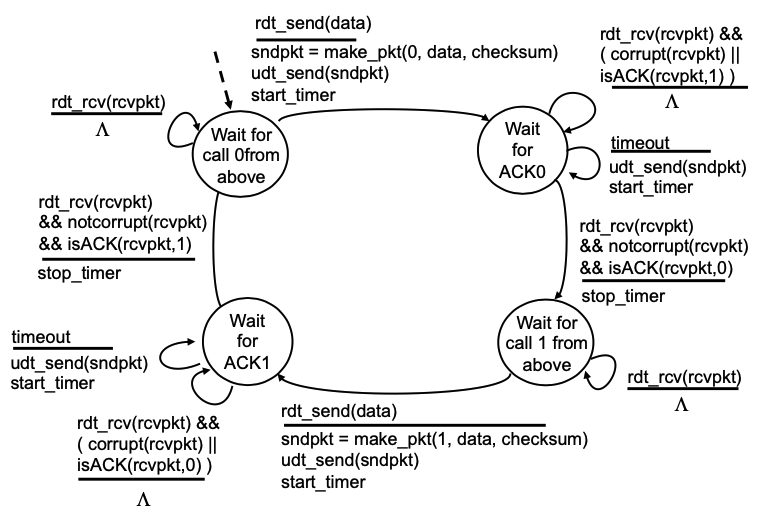
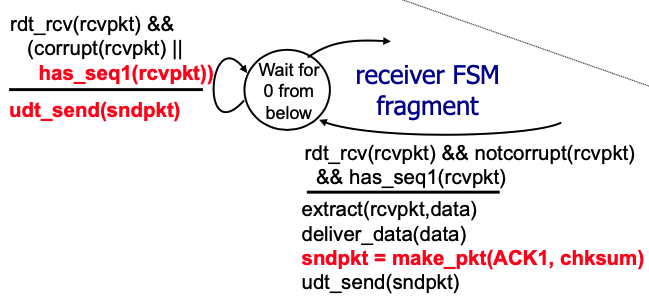
- RDT (Reliable data transfer):
- Go-back-N & selective repeat:
- Go-back-N: Send N unacked packets in pipeline; Receiver only sends cumulative ACK; Sender has timer for oldest unacked packet;
- Selective repeat: Send N unacked packets in pipeline: Receiver send individual ack for each; Sender has timer for each packet.
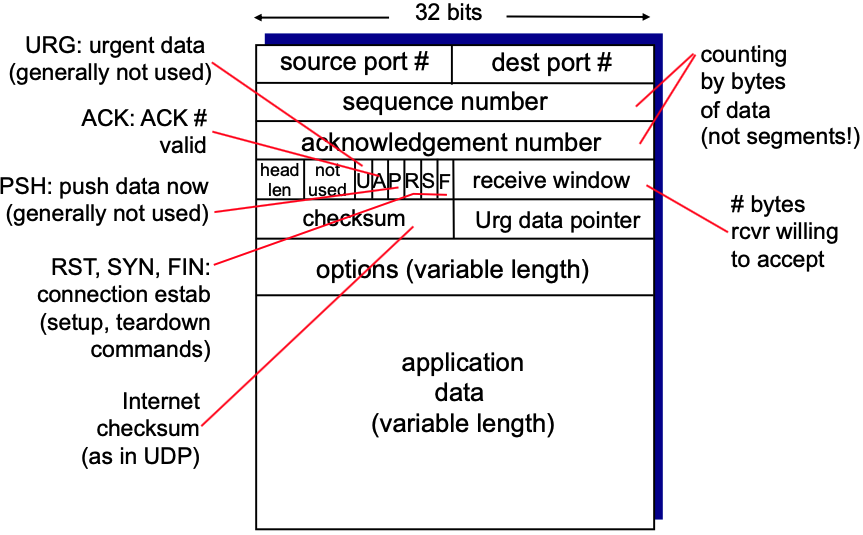
- TCP segment structure:
- Timeout interval for TCP:
- EstimatedRTT = (1 - α) * EstimatedRTT + α * SampleRTT, α can be 0.125;
-
DevRTT = (1 - β) * DevRTT + β * SampleRTT - EstimatedRTT , β can be 0.25; - TimeoutInterval = EstimatedRTT + 4 * DevRTT.
- TCP fast retransmit: If sender receives 3 ACKs for same data (triple duplicate ACK), resend unacked segment with smallest seq # without waiting for the timeout.
- TCP flow control: Receiver “advertises” free buffer space by including rwnd (free buffer space size).
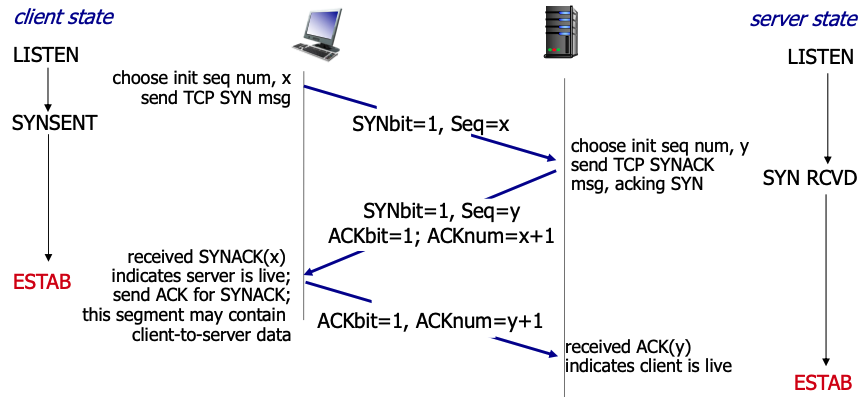
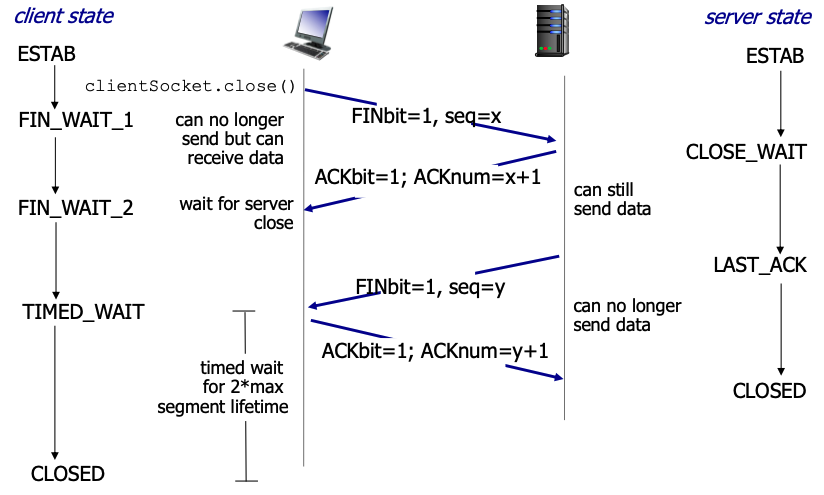
- TCP building a connection and closing a connection:
- TCP congestion control:
- MSS: Maximum segment size;
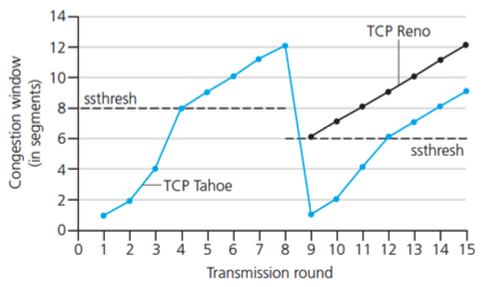
- AIMD: Additive increase (increase cwnd by 1 MSS every RTT until loss); Multiplicative decrease (cut cwnd in half after loss);
- Slow start: Initially cwnd = 1 MSS, double cwnd every RTT until first loss event;
- TCP Reno & TCP Tahoe:
- TCP is fair.
- ECN (Explicit congestion notification): Two bits in IP header marked by router to indicate congestion.
Chapter 4
- Data plane & control plane:
- Data plane: Per-router function, forwarding function;
- Control plane: Network-wide logic, two approaches:
- Traditional routing algorithms: Implemented in routers;
- SDN (Software-defined networking): Implemented in (remote) server.
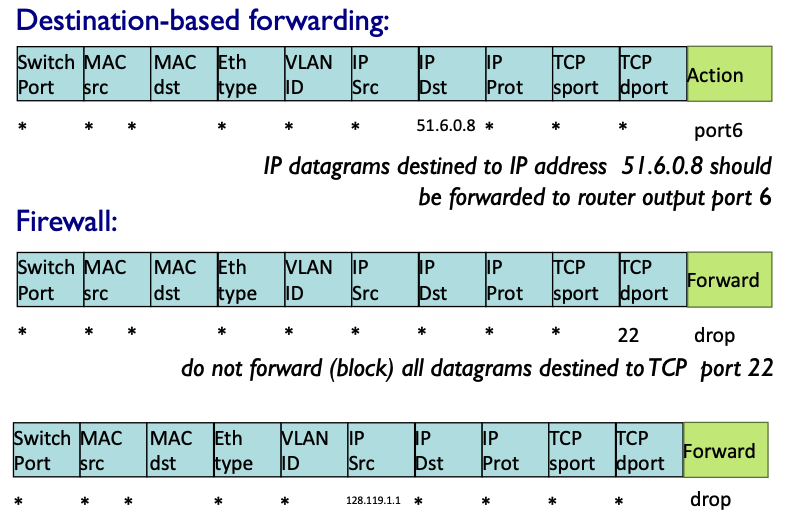
- Destination-based forwarding is using longest prefix matching: Often preformed using TCAMs (ternary content addressable memories).
- Content addressable: Present address to TCAM, retrieve address in one clock cycle, regardless of table size.
- Switching fabrics: Memory, bus, crossbar.
- HOL (Head-of-the-Line) blocking.
- Input buffer overflow and output port buffer overflow can both lead to queueing delay and loss.
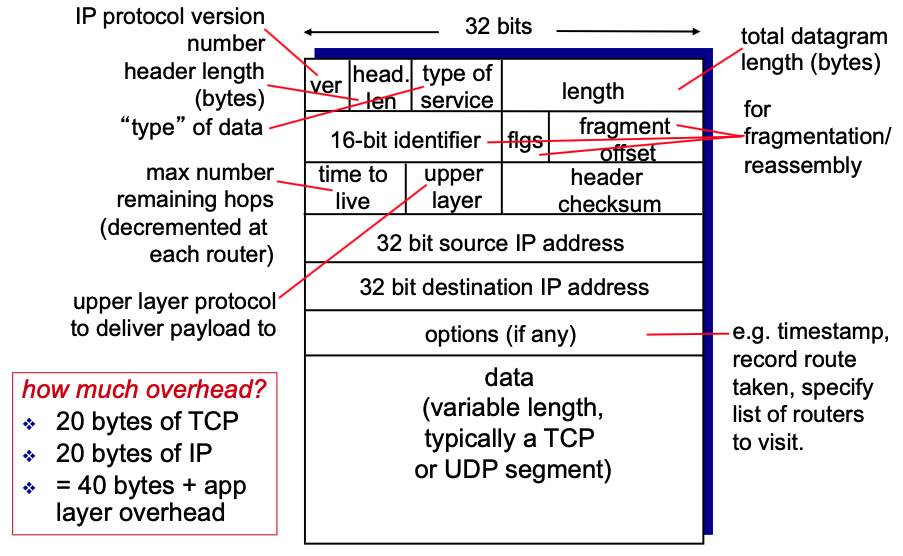
- IP datagram format:
- Network links have MTU (max transfer size), so large IP datagram divided into smaller (fragmented) datagrams and “reassembled” only at final destination.
- One IP address (32-bit) per interface.
- Subnet: Device interfaces with same subnet part of IP address, can physically reach each other without intervening router. Isolated islands when you remove the routers.
- CIDR (Classless InterDomain Routing): a.b.c.d/x.
- DHCP (Dynamic Host Configuration Protocol): Dynamically get address from a server:
- Host broadcasts “DHCP discover” (optional);
- DHCP server responds with “DHCP offer” (optional);
- Host requests IP address: “DHCP request”;
- DHCP server sends address: “DHCP ack”;
- DHCP can return more than just allocated IP address:
- First-hop router;
- Name and IP of DNS server;
- Network mask.
- NAT (Network address translation): All datagrams leaving local network have same single source NAT IP address, but different source port number.
- IPv6 datagram format:
- Fixed-length 40 byte header & no fragmentation allowed;
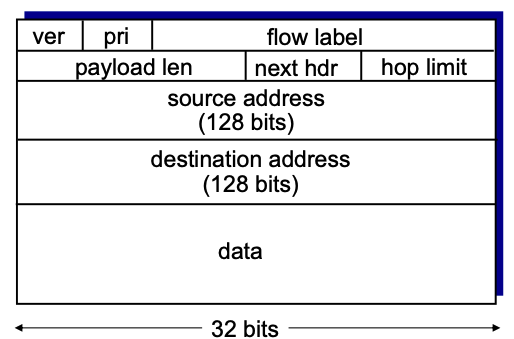
- Tunneling: IPv6 datagram carried as payload in IPv4 datagram among IPv4 routers.
- OpenFlow: Match + action to unify different kinds of devices (router, switch, firewall, NAT). Examples:
Chapter 5
- Dijkstra’s algorithm:
- A link-state routing algorithm;
- https://ranthot.cn/2018/10/09/%E7%AE%97%E6%B3%95%E6%9C%9F%E4%B8%AD%E5%A4%8D%E4%B9%A0%E7%AC%94%E8%AE%B0.html;
- Oscillations possible.
- Bellman-Ford algorithm:
- Distance vector algorithm;
- Each node sends its own distance vector estimate to neighbors, when x receives new DV, it updates its own DV using B-F:
- Dx(y) = minv{c(x, v) + Dv(y)}.
- Iterative, asynchronous, distributed;
- Count to infinity problem & poisoned reverse & split horizon: https://www.geeksforgeeks.org/route-poisoning-and-count-to-infinity-problem-in-routing/.
- Scalable routing:
- AS (Autonomous system).
- Intra-AS routing, also known as IGP (Interior gateway protocols):
- RIP (Routing Information Protocol);
- OSPF (Open Shortest Path First, IS-IS (Intermediate System to Intermediate System) is essentially same as OSPF):
- Using link-state algorithm (Dijkstra’s algorithm) over IP;
- Support security, can have multiple same-cost paths, support both uni- and multi-cast, can be hierarchical.
- IGRP (Interior Gatewat Routing Protocol).
- Inter-AS routing:
- BGP (Border Gateway Protocol):
- eBGP: Obtain subnet reachability information from neighboring ASes;
- iBGP: Propagate reachability information to all AS-internal routers;
- Exchange over TCP connection;
- Hot potatp routing: Choose local gateway with least cost, don’t worry about inter-domain cost.
- BGP (Border Gateway Protocol):
- Intra-AS can focus on performance, while for inter-AS, policy may dominate over performance.
- Problems with traditional routing algorithms: Can’t manipulate routes, do load balancing. But SDN can achieve that.
- ICMP: Internet control message protocol:
- Network-layer “above” IP: ICMP carried in IP datagrams;
- Used to report errors (unreachable host), echo request/reply (ping).
- SNMP (Simple network management protocol), MIB (Management Information Base).
Chapter 6
- Link layer implemented in “adaptor” (network interface card NIC) or on a chip.
- Cyclic redundancy check:
- Let D be the data, G be r+1 bits generator, R be r CRC bits;
- R = remainder(D * 2r / G);
- Can detect all burst errors less than r+1 bits.
- MAC protocols:
- Channel parititioning:
- TDMA: Time division multiple access;
- FDMA: Frequency division multiple access;
- Random access protocols:
- Slotted ALOHA: If collison, retransmit frame in subsequent slot with probility p until success. Efficiency: 37%;
- ALOHA: Similiar to slotted ALOHA, but no slots. Efficiency: 18%;
- CSMA (Carrier sense multiple access):
- If channel sensed idle: transmit. Collisions can still occur due to delay;
- CSMA/CD: Collisions detected within short time and aborted; Binary (exponential) backoff after collision.
- Taking turns: Polling from central site, token passing.
- Channel parititioning:
- MAC address (48 bits).
- ARP (Address resolution protocol): A wants to send datagram to B, A broadcasts ARP query, B receives it and reply to A with its MAC address, A caches IP-MAC pair.
- Ethernet: “Dominant” wired LAN technology.
- Physical topology: bus, star.
- Switch:
- Maintain a self-learned switch table;
-
if entry found for dest: if dest from which frame arrived: drop else: forward frame else: flood
- VLAN (Virtual Local Area Network): Multiple virtual LANs over single LAN infrastructure.
- Multiprotocol label switching (MPLS): High-speed IP forwarding using fixed length label (instead of IP address), using information of both src and dest.